THE BLOG
In this week's video, we look at creating a basic bash script in Kali Linux, a topic from a recently completed Ethical Hacking for Beginners course.
Enjoy the training!
This week's training video is a sample from our recently released SCOR (350-701) Video Training Series, which you can find over on our website.
Specifically, this week's video considers IOCs, wh...
Charles has been wrapping up production on the SCOR (350-701) Video Training Series this week, so we thought it’d be fitting to go over one of the topics on the blueprint with you!
In this video...
In this week's video, Charles looks at data loss prevention (DLP) policies within the Cisco Email Security Appliance (ESA), a security solution outlined in the SCOR (350-701) exam blueprint.
Enjoy ...
As a redundancy measure, it’s possible to deploy multiple Cisco ASAs together in a failover configuration, also known as a High Availability Implementation. This requires that the ASAs have identical ...
Cisco Zone-Based Policy Firewalls are a more modern implementation of the interface-based stateful inspection. This allows you to group interfaces into zones, which have similar functions or features....
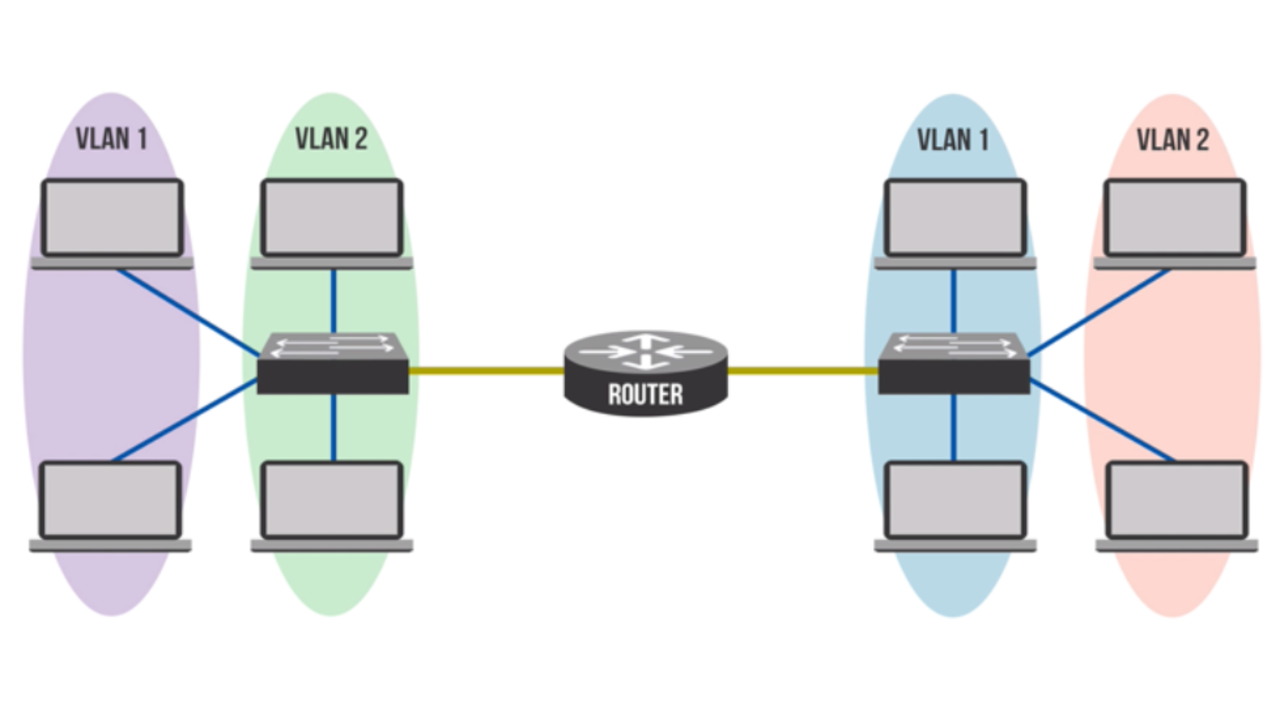
A Virtual Local Area Network (VLAN) is a logical grouping of devices on one or more LANS, configured to communicate as if they were on the same segment. In order to communicate with devices in another...
Our organizational IT environments are constantly changing, driven by factors such as telecommuting, cloud technologies, and BYOD (Bring Your Own Device) policies. This requires modular and dynamic ar...
One question that I get asked all the time goes something like this: “How can I break into the cybersecurity field without any experience?” We hear the stats all the time about zero-percent cybersecur...